In 2025, digital advertising faced its toughest security challenge yet. What used to be simple click fraud has evolved into a complex, self-sustaining ecosystem of scams: malvertising, cloaking, AI-generated creatives and spoofed traffic across web, mobile and CTV.
The scale is massive: industry data shows that more than one in five ad impressions worldwide is invalid or unsafe. Behind those numbers are lost budgets, frustrated users and damaged trust.
For publishers, it means revenue leakage and angry audiences. For advertisers, it means campaigns that look successful on paper but never reach a real audience.
This growing complexity has made security collaboration essential: no single player can solve it alone. That’s why ad fraud has become the number-one business risk in digital media, impacting both the top line and the user experience. This is exactly why MGID and GeoEdge are working together to build a cleaner, safer and more transparent advertising ecosystem.
Ready? Scroll down to start reading!
Table of contents
Click on any chapter to scroll directly to it.
Chapter 1
The State of Digital Advertising in 2025
As digital advertising expands across channels and formats, automation has outpaced transparency, making it harder to see where value is created or lost.
GeoEdge research shows that, across billions of analyzed impressions, malicious ad volume climbed month over month and peaked in June 2025, the highest level seen in the last 12 months. That spike coincided with a global rise in auto-redirect activity.
Programmatic Transparency & Supply Chain Losses
While the programmatic ecosystem in 2025 runs on automation, it is also subject to opacity. Every ad impression passes through a chain of intermediaries: ad exchanges, supply-side platforms (SSPs), demand-side platforms (DSPs), verification vendors. Each layer adds efficiency, but also creates blind spots where money leaks and malicious actors can hide.
GeoEdge’s Global Programmatic Malvertising Index shows that 23 countries worldwide now exceed the 0.5% user safety threshold: proof that malvertising is no longer a localized issue but a global one.
- Severe-risk (5%+) — Russia, Croatia
- High-risk (1-5%) — United Kingdom, Canada, Australia, Malaysia, Vietnam, Saudi Arabia, Denmark, Morocco
- Moderate-risk (0.5-1%) — United States, Spain, Mexico, Singapore, UAE
This growing geographic spread highlights how deeply malicious activity has penetrated the programmatic supply chain.
Recent ANA findings show that advertisers still lose 15–25% of every programmatic dollar to hidden fees, unverifiable inventory or outright invalid traffic. These hidden costs are the direct cause of drained revenue rather than being mere inefficiencies.

To understand how deep this goes, it helps to look at the supply side itself.
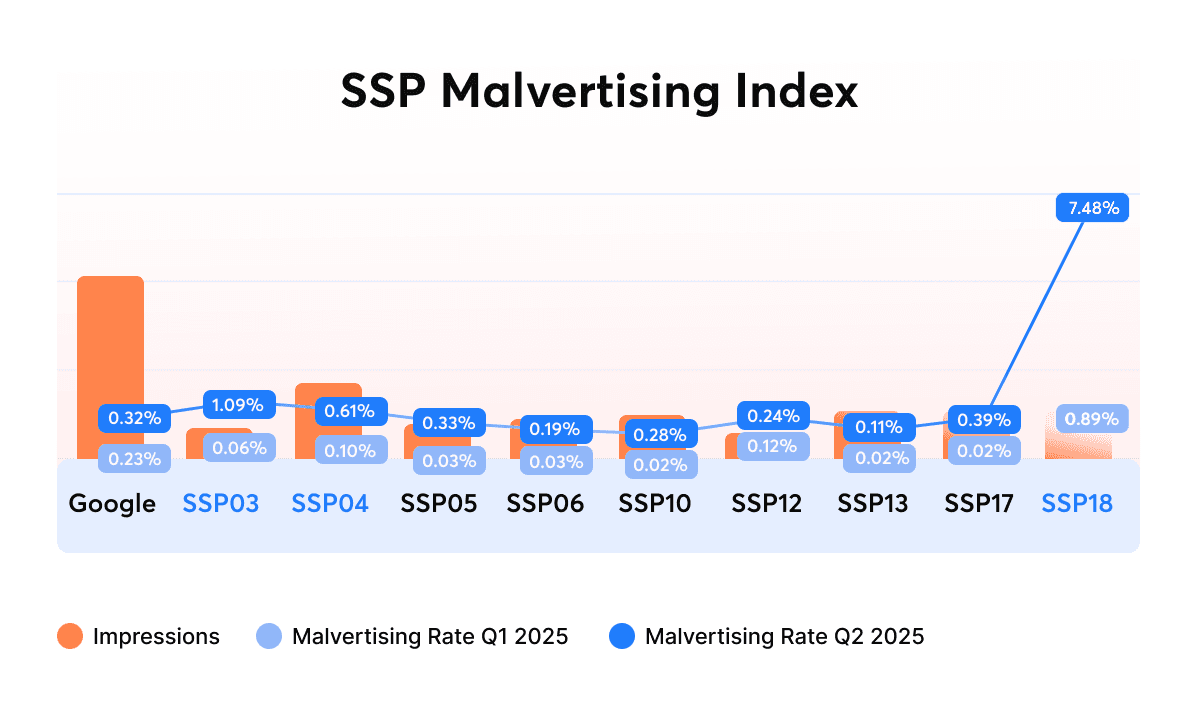
Supply-side platforms (SSPs) are the systems that connect publishers’ ad inventory to buyers across exchanges. Each SSP handles billions of ad impressions monthly, and their security performance can vary widely.
GeoEdge’s Q2 2025 ad quality report revealed major differences between leading SSPs:
- Some, like smaller private SSPs, maintained near-zero malvertising rates.
- Others, including global platforms used by premium publishers, saw malicious ads slip through at alarming rates.
🟦 Fact Box — Supply Chain Health (Q2 2025)
| SSP category | Malvertising rate | Summary |
|---|---|---|
| Top-performing (e.g., SSP06) | ~0.03% | Among the cleanest in the ecosystem with minimal security incidents. |
| Mid-tier (e.g., SSP03, SSP04) | 0.6–1% | Occasional malicious ads, mostly redirects and tech-support scams. |
| High-risk (e.g., SSP18) | Up to 7.5% | High concentration of redirect-based attacks, particularly in Japan. |
The UK and Canada emerged as global hotspots, with 1 in 40 and 1 in 35 impressions flagged as malicious respectively. Both markets were heavily hit by redirect and tech-support campaigns that originated from shared fraud infrastructure. Even in traditionally low-risk regions like Japan and Germany, malvertising rates tripled quarter-over-quarter.
These numbers illustrate how ad quality can degrade as inventory moves across multiple hands. Even trusted supply chains are only as strong as their weakest link.
- For advertisers, that means one compromised SSP can corrupt thousands of campaigns.
- For publishers, it means contaminated demand can erode yield and audience trust.
Transparency now serves as a key element of brand safety. By ensuring clean supply paths, companies protect their revenue, relationships and reputation.
Connected TV (CTV) and Emerging Channels
Connected TV was supposed to be digital advertising’s safe zone: premium environments, long-form content and audience trust. However, even CTV isn’t immune to fraud.
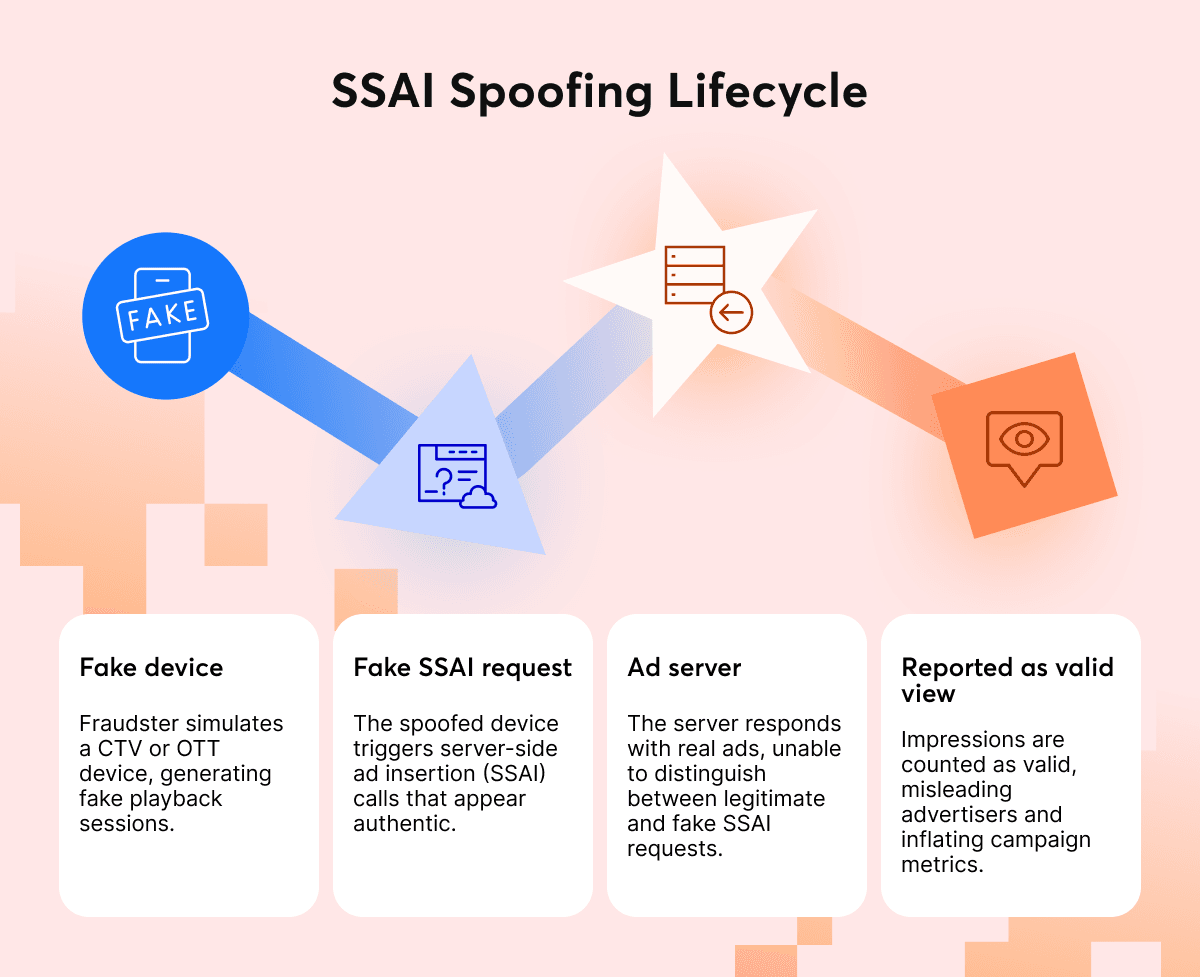
As more ad budgets move from web and mobile into streaming, fraudsters follow the money. The closed, server-to-server (SSAI) structure of CTV delivery gives attackers new ways to hide invalid traffic behind what looks like legitimate viewing. In practice, this means fake streams, spoofed devices and non-human impressions, all blended into reports that seem perfectly normal.
Industry data shows that around 18% of all CTV ad impressions in Q2 2025 were invalid, with a large share linked to SSAI spoofing and device impersonation. That’s nearly one in five ads never seen by a real viewer, an enormous efficiency gap for advertisers and a credibility issue for platforms.
| 🟦 Fact Box — CTV at a Glance (Q2 2025) |
|---|
| 💡 18% of all Connected TV (CTV) ad impressions were identified as invalid traffic (IVT), driven primarily by device spoofing and SSAI manipulation. |
| 💡 SSAI spoofing remains the leading CTV fraud vector, as fraudsters mimic legitimate server-to-server ad requests. |
| 💡 Open exchange inventory is roughly 3x more likely to contain IVT compared with private marketplace (PMP) deals. |
| 💡 Despite rising fraud exposure, global CTV ad spend grew ~20% year-over-year in the first half of 2025. |
Despite these alarming figures, CTV’s ‘walled garden’ perception often gives buyers a false sense of safety. The truth is, emerging channels like CTV, in-app video and digital audio are all being hit by the same forces that reshaped the open web years ago: automation, opacity and scale.
- For publishers, that means enforcing stricter SSP and demand partner controls.
- For advertisers, it’s about asking tougher questions: Who owns the traffic? How was it verified? What portion of my spend is truly viewable by a human?
Made-for-Advertising (MFA) and Low-Value Inventory
Not all threats to digital advertising come from fraudsters with bots. Some are created by the industry itself in the form of made-for-advertising (MFA) sites. These are pages designed primarily to host ads rather than meaningful content: slideshows, auto-refreshing pages, click-bait headlines and long chains of programmatic placements that exist solely to generate impressions.
Premium vs MFA Inventory
| Metric | Premium inventory | MFA inventory |
|---|---|---|
| User engagement | 🟩 High | 🟥 Low |
| ROI | 🟩 Strong, consistent | 🟥 Unstable, short-term |
| Ad density | 🟩 Balanced | 🟥 Excessive |
| Brand trust | 🟩 High | 🟥 Low |
| Risk level | 🟩 Low | 🟥 High |
MFA inventory may not qualify as fraud, but it behaves like it, draining budgets and eroding trust.
- Advertisers may see high viewability and CTR metrics, yet the audiences are disengaged, bouncing after a few seconds or ignoring the ads entirely.
- For publishers, MFA erodes long-term yield because it pushes buyers to prioritize cheap volume over real quality.
| 🟦 Fact Box — MFA by the Numbers (2025) |
|---|
| 💡 MFA inventory accounts for an estimated 12–15% of global programmatic impressions. |
| 💡 Advertisers report up to 20% lower ROI on MFA placements compared to premium content sites. |
| 💡 70% of buyers say MFA content “hurts brand perception,” even when it meets viewability benchmarks. |
MFA content also makes the ecosystem more vulnerable to ad quality issues: intrusive formats, hidden redirects and low editorial control all create fertile ground for malvertising. In short, MFA may not always break the rules, but it breaks trust.
Beyond content quality, MFA environments are also where user experience takes the hardest hit. GeoEdge’s Q2 2025 User Experience Impact data shows that floating ads have increased eightfold since 2024, especially in North America and Europe, while heavy ad creatives reached record levels in June. These oversized or intrusive formats slow down page performance (LCP, CLS) and drive bounce rates higher, directly reducing engagement and long-term publisher revenue.
As the market matures, the smartest advertisers are shifting focus from “cheap reach” to verified environments where human attention, transparency and safety go hand in hand. For publishers, the path forward is clear: sustainable revenue depends on ad experiences that respect both the brand and the audience.
Ad Quality Landscape
If 2024 was the year ad fraud went quiet, 2025 is the year it came back louder and smarter. Malvertising, cloaking and intrusive ad formats have evolved beyond nuisance. They now pose real financial and reputational risks for every player in the ecosystem.
Across billions of impressions analyzed in the first half of 2025, malicious and low-quality ads are on the rise, flooding the ecosystem.
GeoEdge data shows that redirect-based attacks dominate the threat landscape, rising from 48% in Q1 to 66% in Q2, while tech support scams and malicious extensions surged across mobile and desktop.
In Q2 2025, malicious ad activity doubled across the top five markets. Redirect-based attacks surged 37%, now accounting for 66% of all malicious ads, while tech-support scams rose sharply to 18%. Floating ads continued to explode and were eight times higher than in 2024, cementing their status as the leading UX disruptor worldwide.
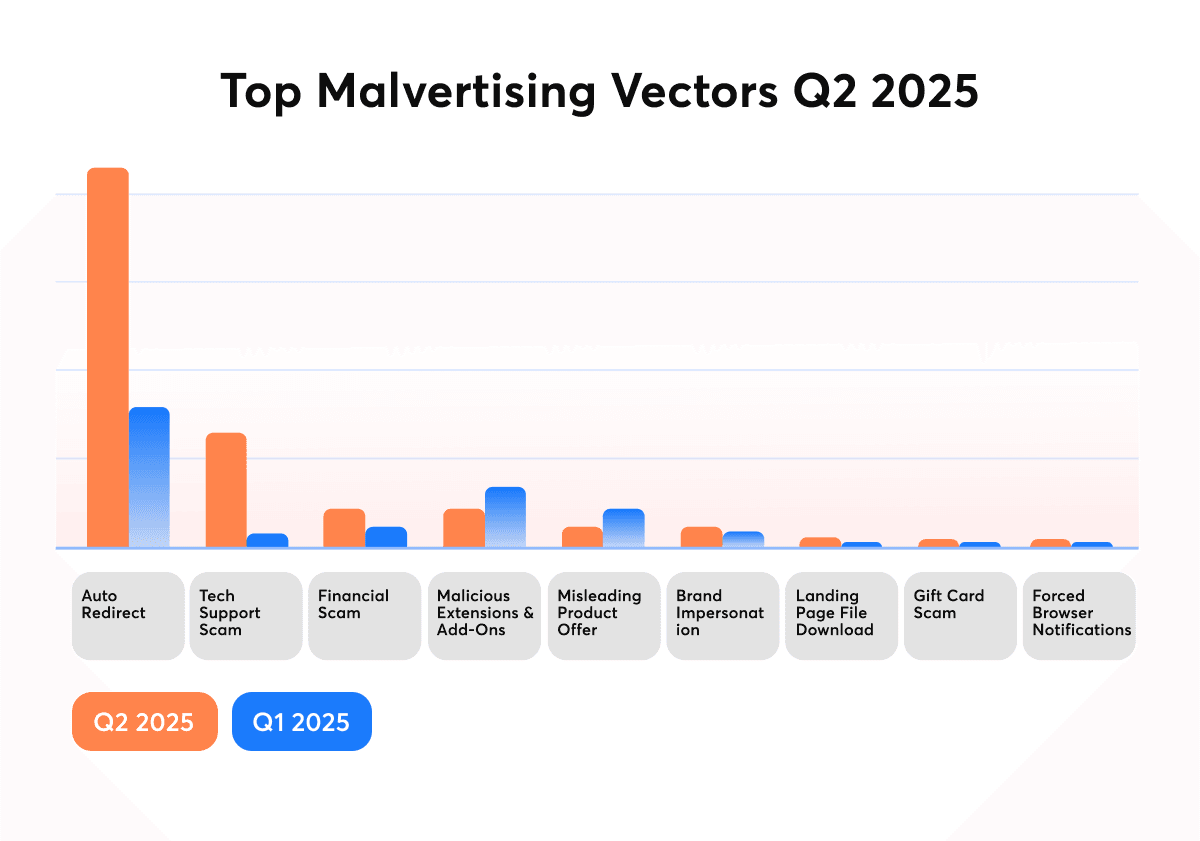
These attacks often masquerade as harmless creatives but hijack user sessions, trigger fake redirects or install unwanted software. Mobile users remain the biggest target: nearly three-quarters of all incidents in Q2 occurred on mobile devices, a trend that continues to climb.
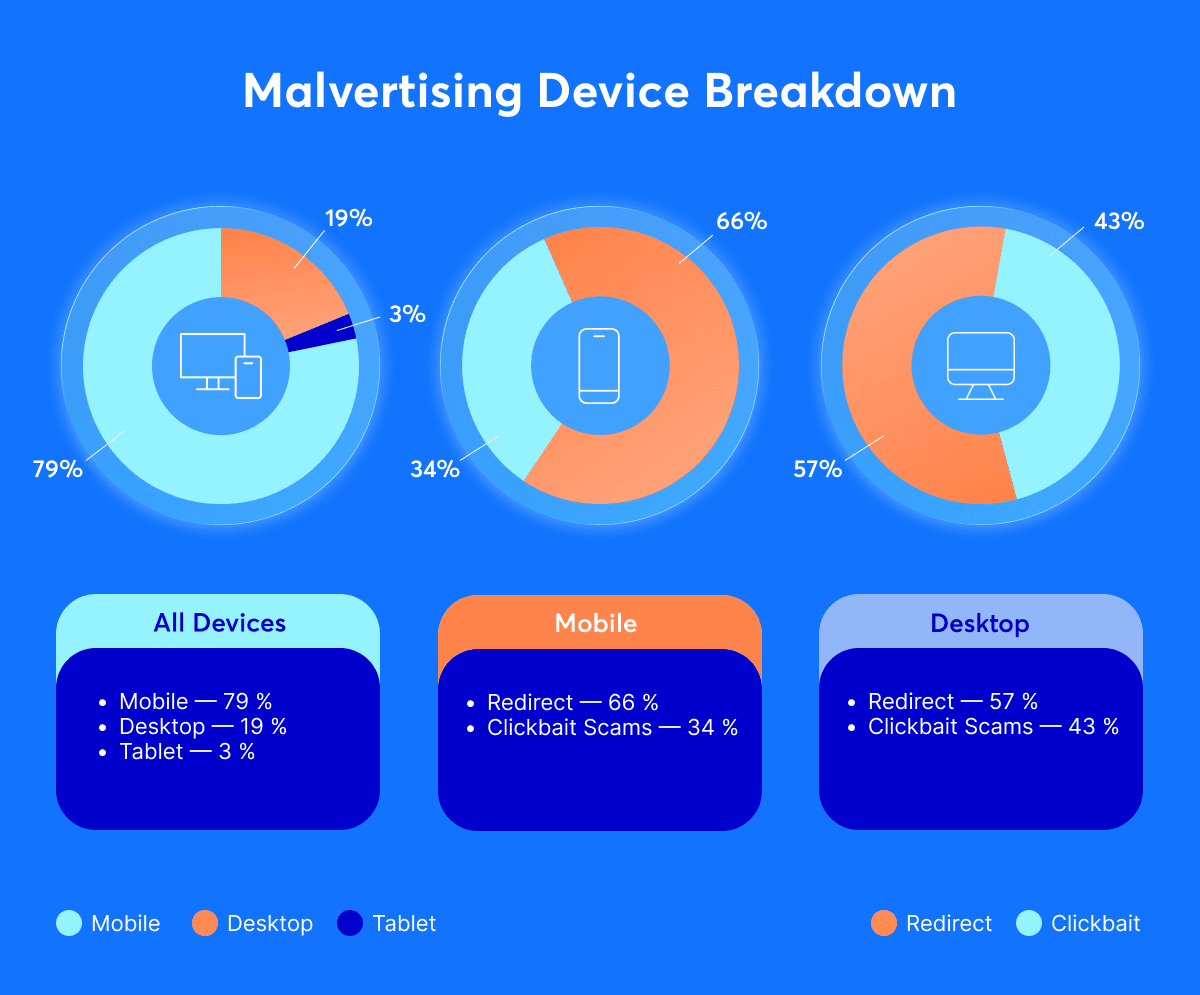
| 🟦 Fact Box — Ad Quality Snapshot (H1 2025) |
|---|
| 💡 1 in 130 ad impressions is malicious. |
| 💡 66% of malicious activity comes from auto-redirects. |
| 💡 21% of malicious ads use cloaking to hide their true content. |
| 💡 Floating ads doubled vs. last quarter (58% mobile, 40% desktop) and are now one of the top UX complaints. |
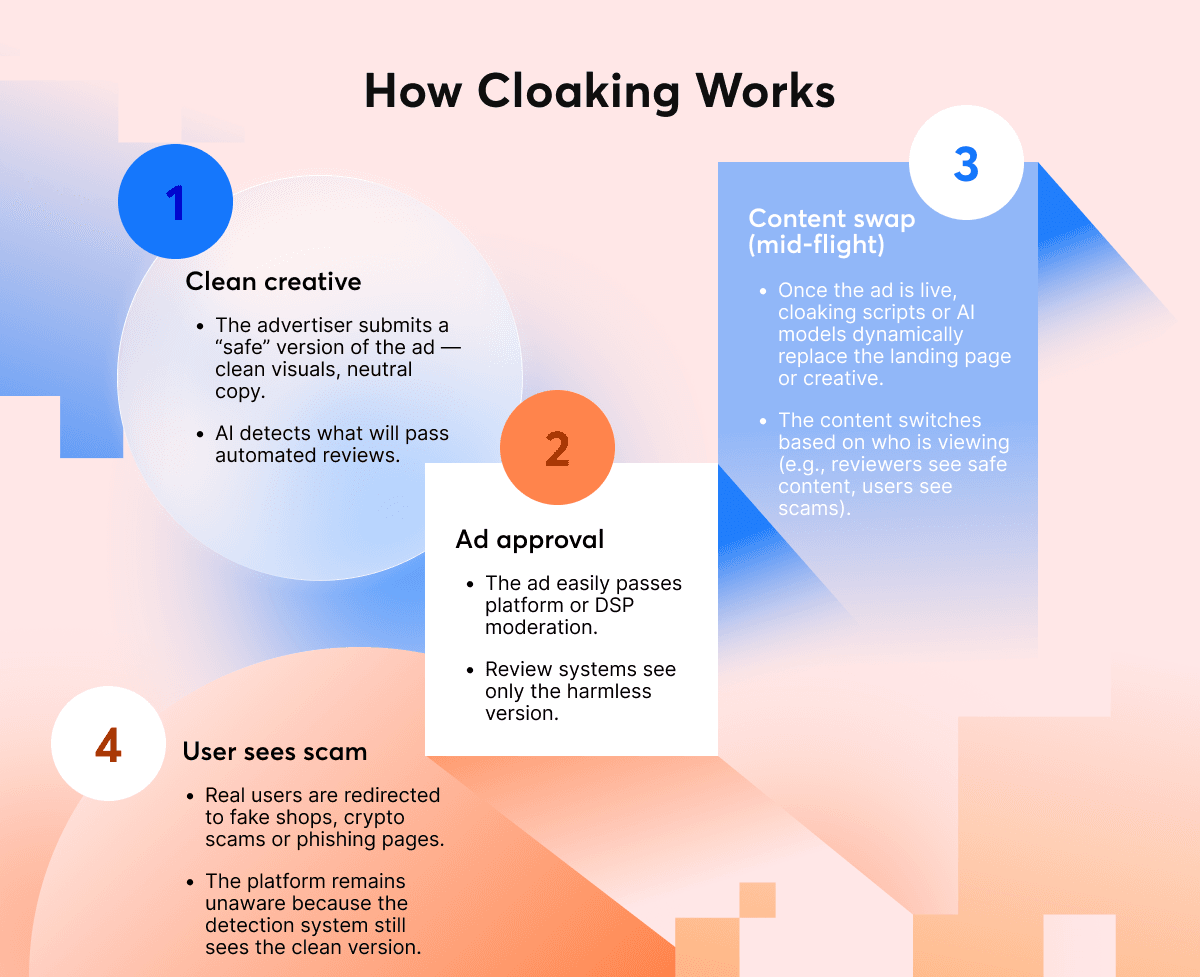
Cloaking has become a particularly slippery problem. Fraudsters now use AI-based content swapping and fingerprinting to show “clean” creatives during moderation and then replace them with scams or misleading claims once creatives are approved. Meanwhile, floating and autoplay ads are wearing down user trust. In Q2, 60% of users said these formats ruin their experience, directly impacting engagement, time on site and ultimately publisher revenue.
The result is a perfect storm: malvertising is scaling faster than detection, and user patience is at an all-time low. For both advertisers and publishers, the message is clear: ad quality is a necessary metric for survival.
Standards and Compliance
In a digital ecosystem that moves faster than any regulation, standards are the closest thing we have to trust. Organizations like TAG (Trustworthy Accountability Group), IAB (Interactive Advertising Bureau) and the Media Rating Council (MRC) exist for one reason: to help advertisers and publishers prove they’re doing things transparently, safely and consistently.
- TAG certification, for example, requires companies to implement strict anti-fraud, anti-malware and brand safety controls.
- IAB and MRC guidelines go a step further, defining how to measure impressions, viewability and invalid traffic, so everyone plays by the same rules.
Standards Ecosystem Map
| Layer | Focus | Description |
|---|---|---|
| TAG (Trustworthy Accountability Group) | 🛡️ Fraud prevention | Establishes anti-fraud standards and certification frameworks to secure the ad supply chain. |
| IAB (Interactive Advertising Bureau) | 📖 Transparency & policy | Defines advertising policies, transparency principles and ethical standards for responsible media buying. |
| MRC (Media Rating Council) | 📊 Measurement & verification | Audits and accredits metrics, ensuring that impressions and engagement are measured accurately and transparently. |
| MGID × GeoEdge | ⚙️ Implementation layer | Applies these standards in real time, verifying ad quality, preventing fraud and maintaining brand-safe environments. |
The real value lies in credibility, as opposed to compliance. Advertisers increasingly favor TAG Certified supply chains, and publishers with verified partners see measurable gains in CPMs and renewal rates. According to IAB’s 2025 transparency survey, advertisers are 30% more likely to allocate spend to TAG-verified platforms because they can trace where their money goes.
| 🟦 Fact Box — Why Certification Matters |
|---|
| 💡 TAG certified channels report up to 80% lower IVT than uncertified ones. |
| 💡 30% of advertisers say TAG/IAB compliance is now a key buying criterion. |
| 💡 MRC-accredited measurement improves campaign transparency and ROI reporting accuracy by 25–40%. |
The latest GeoEdge data highlights why certification and continuous monitoring must go hand in hand. Even trusted SSPs like SSP03 and SSP04 showed malvertising growth in Q2, reinforcing that TAG-aligned verification and real-time blocking are imperative for businesses.
At the same time, certification alone isn’t a silver bullet. Fraudsters adapt faster than standards can evolve, which is why continuous monitoring, threat intelligence and proactive ad scanning remain essential.
That’s where the partnership between MGID and GeoEdge sets a new baseline for compliance, combining real-time ad verification with policies built on TAG and IAB frameworks. This ensures every impression in MGID’s network is clean and verifiably compliant with industry standards. Because trust today depends on what can be verified.
Regional Ad Policy Landscape
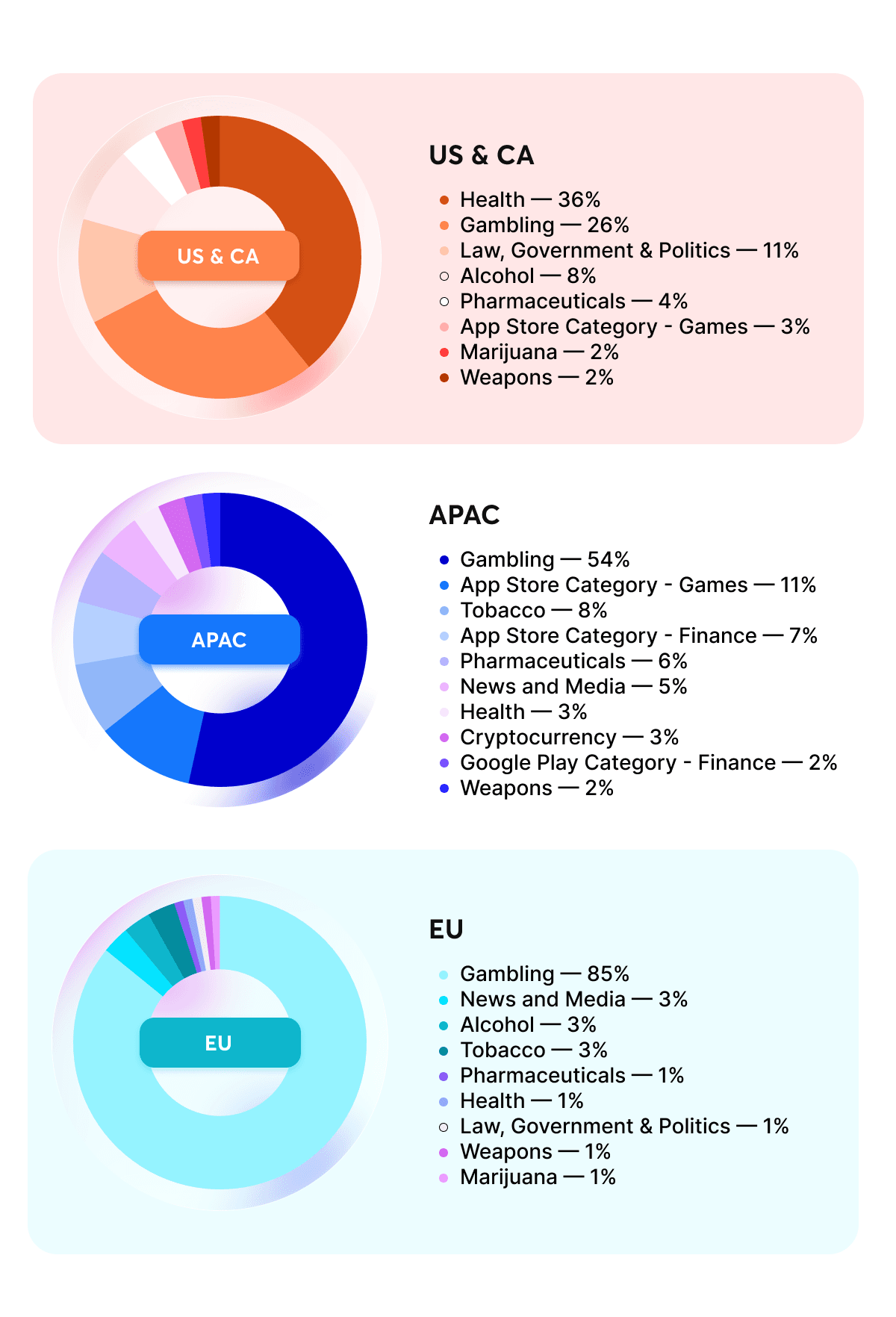
Ad content restrictions are becoming a central part of brand safety strategy. According to a GeoEdge report, in Q2 2025, ad content restrictions intensified worldwide. Health-related ads remained the most blocked category in North America (36%), while Gambling dominated Europe (85%) and APAC (54%). The rise in enforcement around high-risk verticals shows how regulation and platform policies are reshaping the inventory landscape for advertisers and publishers alike.
Chapter 2
Anatomy of Ad Fraud in 2025
Ad fraud has grown into a complex, multi-layered ecosystem. Modern fraudsters build large-scale infrastructures that simulate real engagement, outsmart detection and infiltrate the entire ad supply chain. In 2025, the line between technical fraud and creative deception has almost disappeared.
Here’s how these main fraud families connect across the advertising ecosystem.
Invalid Traffic (GIVT & SIVT)
At its simplest, Invalid Traffic (IVT) is any impression, click or conversion that doesn’t come from a real human.
Although, not all IVT is the same. There’s General IVT (GIVT), which is easy to spot and filter (like known bots or data-center IPs), and then there’s Sophisticated IVT (SIVT), a much harder to detect practice because it imitates human behavior at scale.
| How it works |
|---|
| 1️⃣ Fraudsters infect thousands of devices or build virtual ones (emulators, spoofed browsers). |
| 2️⃣ These devices send ad requests with real-looking metadata: OS, screen size, location. |
| 3️⃣ The ad gets served, counted and paid, but no one ever sees it. |
| 4️⃣ Revenue flows to fake publishers or resellers down the chain. |
SIVT now powers most large-scale ad fraud, especially on mobile and CTV. It’s what turns simple fake clicks into billion-dollar botnets.
Malvertising & Scam Ads
While IVT steals budgets invisibly, malvertising attacks the user directly. It injects harmful or deceptive ads into legitimate placements, redirecting users, loading malware or leading them to phishing pages.
GeoEdge data from early 2025 shows that redirects made up two-thirds of all malicious ad activity, and mobile users were the main victims.
| How it works |
|---|
| 1️⃣ A fraudulent creative is uploaded and passes platform review. |
| 2️⃣ Once live, it executes hidden code, redirecting the user or prompting a fake alert. |
| 3️⃣ Attackers earn from stolen data, affiliate scams or traffic reselling. |
| 4️⃣ The publisher loses user trust and session revenue. |
These campaigns are increasingly automated, swapping domains and payloads every few hours to stay ahead of detection.
Cloaking 2.0
Cloaking used to be a trick for SEO scammers. Now it’s one of the most advanced ad-fraud tactics. Fraudsters use AI-generated creatives, fingerprinting and behavioral triggers to show a “clean” version of an ad to reviewers and a completely different, often malicious one to real users.
| How it works |
|---|
| 1️⃣ During ad approval, the system sees a compliant landing page. |
| 2️⃣ Once approved, the script identifies real users (by IP, device or region). |
| 3️⃣ The landing page swaps to a scam or malware payload. |
| 4️⃣ Detection becomes nearly impossible without real-time scanning. |
Cloaking now affects an estimated one in five malicious ads in circulation (GeoEdge internal data, 2025) and is a key reason why manual review alone no longer works.
SSAI Spoofing and CTV Fraud
As discussed earlier, Server-Side Ad Insertion (SSAI), used in CTV and streaming, was meant to improve performance. Instead, it’s become one of the easiest places to fake impressions. Fraudsters send synthetic ad requests that look like legitimate server traffic from streaming devices.
| How it works |
|---|
| 1️⃣ The attacker creates or hijacks an SSAI endpoint. |
| 2️⃣ They simulate thousands of “streams,” generating ad calls in real time. |
| 3️⃣ The ad server counts each as a valid view. |
| 4️⃣ Fraudsters pocket CPM revenue, while advertisers pay for invisible audiences. |
Because SSAI requests come from servers, not end-user devices, traditional anti-bot systems can’t see the difference.
Intrusive and UX-Harming Formats
Some threats don’t even require malware. Ads that autoplay sound, cover content or redirect users create experience fraud, breaking the value exchange between user, publisher and advertiser.
In 2025, floating ads doubled in volume, and 60% of users said they damage trust and make them less likely to engage.
| How it works |
|---|
| 1️⃣ Ads use aggressive formats or overlays to maximize short-term CTR. |
| 2️⃣ Users get frustrated, close the page or block ads altogether. |
| 3️⃣ Publishers lose engagement, and advertisers lose real attention. |
In other words, even when technically “clean,” bad ad experiences still destroy value — slowly but surely.

Takeaway: Ad fraud in 2025 is both technical and psychological. It blends automation, deception and UX manipulation into one ecosystem of loss. Protecting revenue now means defending every layer: the traffic, the creative, the user and the perception.
Chapter 3
Artificial Intelligence: Friend and Foe
Artificial intelligence has changed everything, including ad fraud. By 2025, AI has evolved from analyzing performance to creating ads, generating landing pages and orchestrating entire campaigns. The same technology that helps marketers optimize can also help attackers deceive.
Let’s look at both sides of that coin.
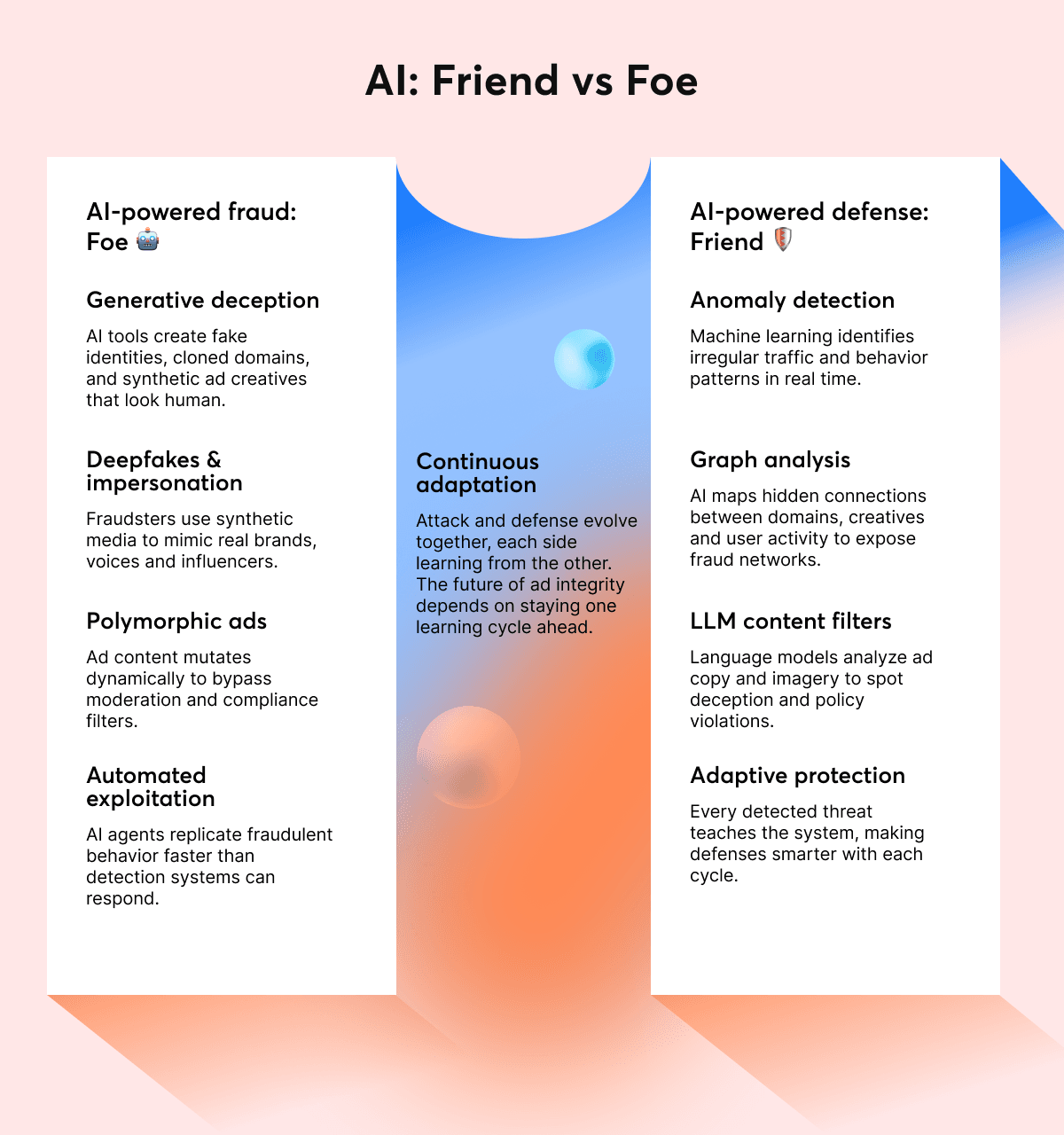
AI-Powered Fraud Tactics
Fraudsters have embraced AI to make their operations faster, cheaper and harder to detect. What used to take hours of manual work (swapping creatives, generating fake domains, writing scam copy) can now happen in seconds through automation.
Attackers use generative AI tools to mass-produce fake creatives, headlines and landing pages that look completely legitimate. They also deploy AI-driven mutation models that constantly change elements of malicious ads (colors, copy, even product images) to avoid signature-based detection.
Some operations go further, using deepfake personas to give their scams a “human” face: a fake founder, a fake endorsement or a synthetic influencer promoting non-existent products.
| 🧰 AI in action — the fraudster’s toolkit |
|---|
| ⚙️ Polymorphic malware: Code that rewrites itself every few hours. |
| ⚙️ LLM-generated scam ads: Endless variations of fake “crypto giveaway” campaigns. |
| ⚙️ AI voiceovers: Cloned celebrity voices promoting fraudulent apps. |
| ⚙️ Deepfake imagery: Convincing “before/after” visuals that bypass creative review. |
AI has effectively lowered the barrier to entry for digital deception. Fraudsters no longer need sophisticated technical skills, just the right prompt.
AI as a Defense
Thankfully, the same tools that fuel fraud are also transforming the way we fight it. Modern ad-security systems, including MGID and GeoEdge, now rely on AI-driven classification and real-time decisioning to identify threats long before users ever see them.
Using large language models (LLMs) and computer vision, these systems can:
- Analyze ad copy and visuals to detect misleading or harmful content.
- Spot “borrowed design” scams that mimic legitimate brand layouts.
- Map domain and network relationships to find coordinated bot activity.
- Flag creatives generated by AI to verify authenticity and disclosure compliance.
| 🧰 AI in action — the defender’s arsenal |
|---|
| ⚙️ Text & image classification: Instantly detects policy violations in ad creatives. |
| ⚙️ Graph-based anomaly detection: Tracks clusters of suspicious domains in real time. |
| ⚙️ Behavioral modeling: Learns what “normal” looks like for a publisher’s traffic and spots deviations within milliseconds. |
| ⚙️ LLM-driven moderation: Automatically reviews creative text for false claims or manipulative language. |
In practice, these systems block bad ads and learn from every attempt they stop. That means each detection makes the next one faster, and the overall ecosystem cleaner.
Chapter 4
MGID × GeoEdge: Unified Defense Against Fraud
The fight against ad fraud is not one that any company can win alone. That’s why MGID partnered with GeoEdge, a global leader in ad security and verification, to build a unified defense system that protects every impression, every user and every partner across the MGID ecosystem.
What started as a security integration has evolved into a strategic alliance, combining MGID’s vast programmatic reach with GeoEdge’s real-time threat detection and AI-powered verification framework.
Long-Term Partnership Overview
MGID’s mission has always been to make advertising safe, transparent and human-centered, and as fraud tactics became more sophisticated, from cloaking and redirects to AI-generated scam creatives, it became clear that manual checks alone weren’t enough.
GeoEdge offered what the market needed: real-time protection and forensic visibility across all ad creatives, channels and devices. Together, the companies have built an integrated solution that’s both preventive and adaptive, stopping threats before they reach users.
| 🛡️ Defense in Motion: Partnership Results |
|---|
| 🔹 90% reduction in compliance issues after full integration |
| 🔹 100% restoration of a clean and secure user environment |
| 🔹 Improved publisher yield through higher ad quality |
Multi-Layer Security Architecture
The MGID × GeoEdge framework is built around three core stages of protection: before, during and after each ad impression.
Pre-Flight: Verification & Prevention
Before any campaign goes live, every advertiser, agency and business partner undergoes a rigorous KYC/KYB verification process to confirm identity and legitimacy.
Once verified, the ad materials move through AI-powered creative scans that analyze each element (text, image, video, landing page) for potential risks:
- Malware or hidden code injections;
- Deceptive design or misleading offers;
- Policy and content violations (e.g., adult, crypto or financial misrepresentation).
Only ads that pass all checks are approved for delivery, ensuring that malicious actors are filtered out before they can enter the advertising ecosystem.
In-Flight: Real-Time Monitoring & Protection
Once campaigns go live, monitoring doesn’t stop there. MGID and GeoEdge systems continuously track every impression, click and redirect in real time to detect:
- Cloaking attempts when ad content switches after approval;
- Redirect chains leading to unsafe or unauthorized destinations;
- Suspicious landing page behavior (e.g., forced installs, pop-ups, phishing prompts).
GeoEdge’s protection engine automatically blocks detected threats within seconds, preventing user exposure and preserving brand safety. At the same time, MGID’s compliance team receives instant alerts to review, verify and respond with further action.
Post-Flight: Analysis, Learning & Reinforcement
After a threat is blocked, the process doesn’t stop, but rather, it evolves. GeoEdge performs a full incident analysis, examining how the attack worked, what patterns it used and where it originated.
This intelligence is then fed directly into MGID’s machine learning models, updating detection signatures and improving future accuracy. Each incident strengthens the system, turning every blocked threat into a new layer of protection for the entire network.
| 🛡️ Defense in Motion: 24/7 Protection Cycle |
|---|
| 1️⃣ Detect: Advanced AI and behavioral algorithms scan every impression, click and redirect in real time, identifying malware, cloaking, phishing patterns and policy violations before users ever see them. |
| 2️⃣ Block: Once a threat is detected, GeoEdge automatically removes or disables the malicious creative within seconds. This ensures that harmful ads never reach live inventory, protecting users, publishers and brands simultaneously. |
| 3️⃣ Analyze: Each incident triggers a full investigation. Threat intelligence teams and automated systems dissect how the attack worked, tracing its origin, structure and evasion methods. |
| 4️⃣ Update: Insights from the analysis feed directly into MGID’s and GeoEdge’s shared databases and machine learning models. Detection signatures, domain blacklists and behavioral rules are updated in real time, making the defense smarter with every cycle. |
| 5️⃣ Prevent: Updated intelligence strengthens pre-flight screening and real-time monitoring. Every blocked or analyzed threat enhances future resilience, reducing the risk of similar attacks reappearing. |
Zero-Tolerance Policy
Both companies operate under a simple principle: malicious content never gets a second chance. Every ad is screened for malware, phishing and deceptive content with zero exceptions.
High-risk verticals (financial services, crypto, health, weight loss and gambling) receive extra scrutiny and manual review by regional compliance teams. By eliminating bad actors, MGID reinforces a foundation of safety and user trust. Because one unsafe ad can undo years of credibility.
Chapter 5
What MGID × GeoEdge Do for Advertisers and Publishers
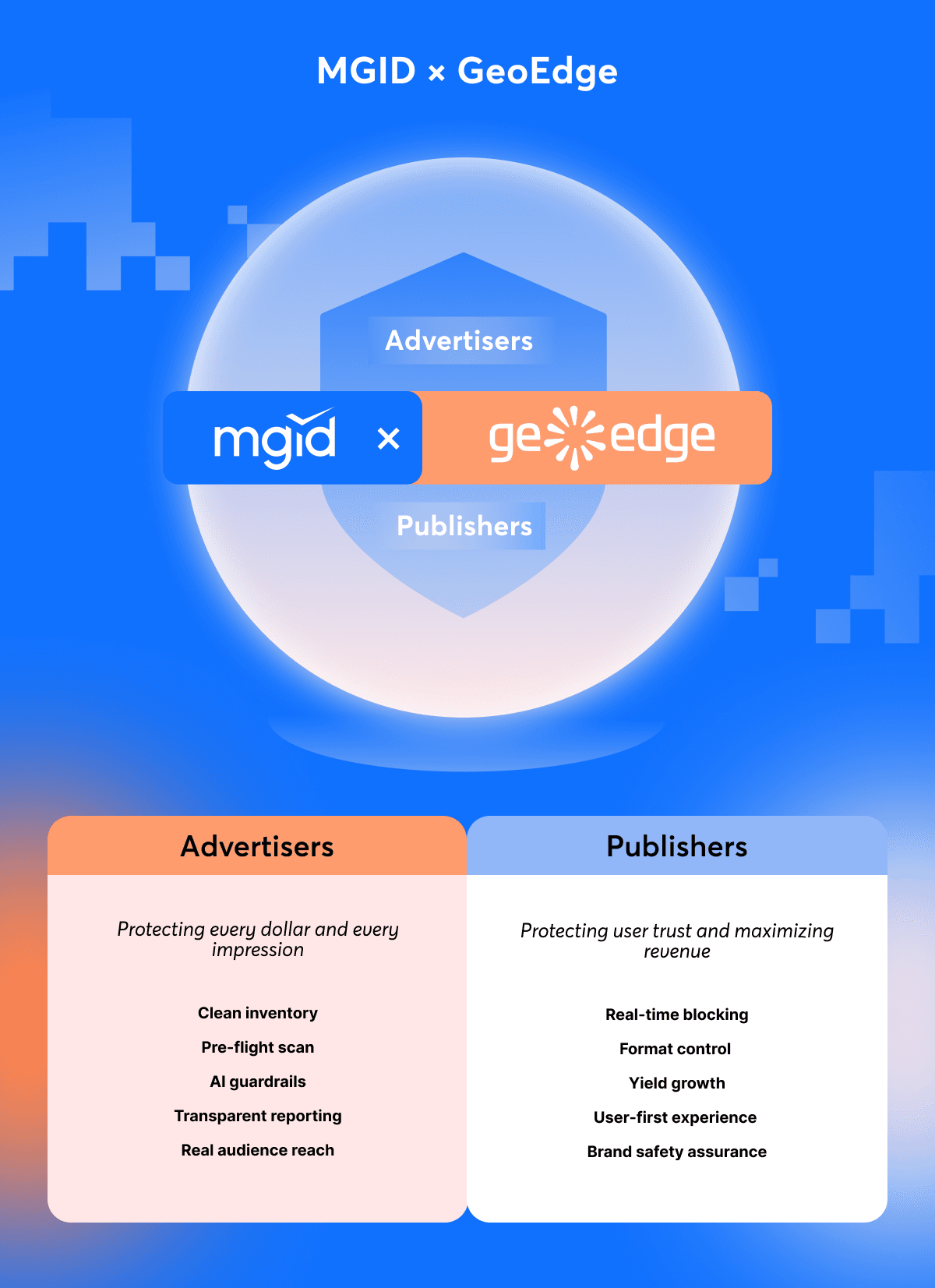
Ultimately, clean advertising is both a moral stance and a measurable advantage. Through the MGID × GeoEdge partnership, both advertisers and publishers receive exactly what they need most: transparency, safety and performance that lasts.
For Advertisers
In a fragmented ecosystem full of hidden risks, advertisers need to know that every dollar they spend reaches a real audience: not bots, not cloaked pages, not fake installs.
MGID and GeoEdge make that possible with a “clean inventory by design” approach.
What that means:
- TAG-certified inventory only: Ads run exclusively through trusted, verified supply paths.
- Pre-flight creative checks: Every ad creative and landing page is scanned for malware, policy violations and compliance risks before launch.
- AI guardrails: MGID’s AI-powered validation tools detect misleading claims, manipulated designs or unverified offers.
- Transparency dashboards: Advertisers get clear reporting on blocked impressions, affected geos, devices and categories.
For Publishers
For publishers, ad quality is directly tied to user trust and revenue. Even one bad ad can cause session drops, lower engagement or even platform blacklisting. MGID and GeoEdge work together to prevent that, giving publishers full control over the advertising experience.
What that means:
- Real-time malvertising protection: Harmful ads and redirects are blocked before they reach the page.
- Control over intrusive formats: Floating units, autoplay video and expandables can be automatically filtered or limited by publisher policy.
- Yield uplift: Clean, trustworthy inventory attracts higher CPMs and long-term advertiser relationships.
- User-first experience: Faster load times, fewer interruptions and higher engagement mean stronger retention.
Chapter 6
Practical Playbooks
Theory is all well and good, but action stops fraud. These playbooks give both advertisers and publishers practical steps to make every campaign and placement safer without slowing down business.
Advertiser Playbook
Running a campaign in 2025 means balancing speed, scale and safety. Here’s how to make sure your ads stay clean from day one.
1. Start with a Secure Brief
- Include compliance criteria in every campaign brief.
- Require transparency on traffic sources and landing pages.
- Ask partners if they’re TAG-certified or verified by GeoEdge/MGID.
2. Validate Landing Pages
- Run every landing page through a verification scan before launch.
- Avoid shortened or masked URLs, as they’re common in cloaking attacks.
- Test pages from different devices and geos to catch region-based redirects.
3. Check Creatives for Policy Risks
- Watch for exaggerated claims (“guaranteed”, “risk-free”).
- Verify AI-generated assets for accuracy and disclosure.
- Ensure visuals don’t mimic well-known brands or government designs.
4. Monitor, Don’t Assume
- Track campaign-level fraud KPIs (blocked impressions, IVT share, redirect events).
- Review GeoEdge incident reports for patterns, not just isolated cases.
- Update creative and targeting rules quarterly to reflect new attack types.
📘 Playbook tip: Treat ad verification like audience targeting: always on, always optimized.
Publisher Playbook
For publishers, trust equals revenue. A single bad ad can drive users away for months. Here’s how to maintain a secure, high-yield ad environment.
1. Set Clear Ad Policies
- Define what’s “acceptable” and what’s not (redirects, floating formats, auto-play).
- Share policies with all SSP and exchange partners.
- Use GeoEdge’s tools to enforce them automatically.
2. Integrate Continuous Scanning
- Enable pre-flight and live ad scanning across all placements.
- Use automated blocking for malware, cloaking and heavy ads.
- Check new ad partners with KYC/KYB verification.
3. Monitor UX and Performance
- Keep an eye on bounce rates and page load times — both of which are early warning signs of bad ads.
- Use Chrome’s Heavy Ad Intervention reports to spot over-weight creatives.
- Run quarterly UX audits with your ad operations team.
4. Build a Response Plan
- Know who to contact when a violation occurs (network, SSP or developer).
- Document every incident: type, impact, resolution time.
- Re-check the domain or campaign before reinstating.
📘 Playbook tip: The faster you isolate a bad ad, the less it costs you in both revenue and reputation.
Incident Response Guide
Even with the best prevention, incidents happen. A quick and transparent response can turn a crisis into an advantage.
| 4-Step Incident Response Plan |
|---|
| 🔹 Detection: Use real-time alerts (GeoEdge, MGID) to identify the issue instantly. |
| 🔹 Isolation: Pause the affected campaign or partner channel. |
| 🔹 Communication: Inform all stakeholders (advertiser, SSP, publisher) within the hour. |
| 🔹 Recovery: Remove malicious assets, perform re-scan and document the outcome. |
📘 Playbook tip: Don’t hide the issue. Transparency builds trust faster than any apology.
Chapter 7
Measuring Success
Effective ad fraud prevention means demonstrating that the system truly works. Success means cleaner traffic, safer user experiences and measurable business impact.
Here’s how MGID and GeoEdge recommend tracking what really matters.
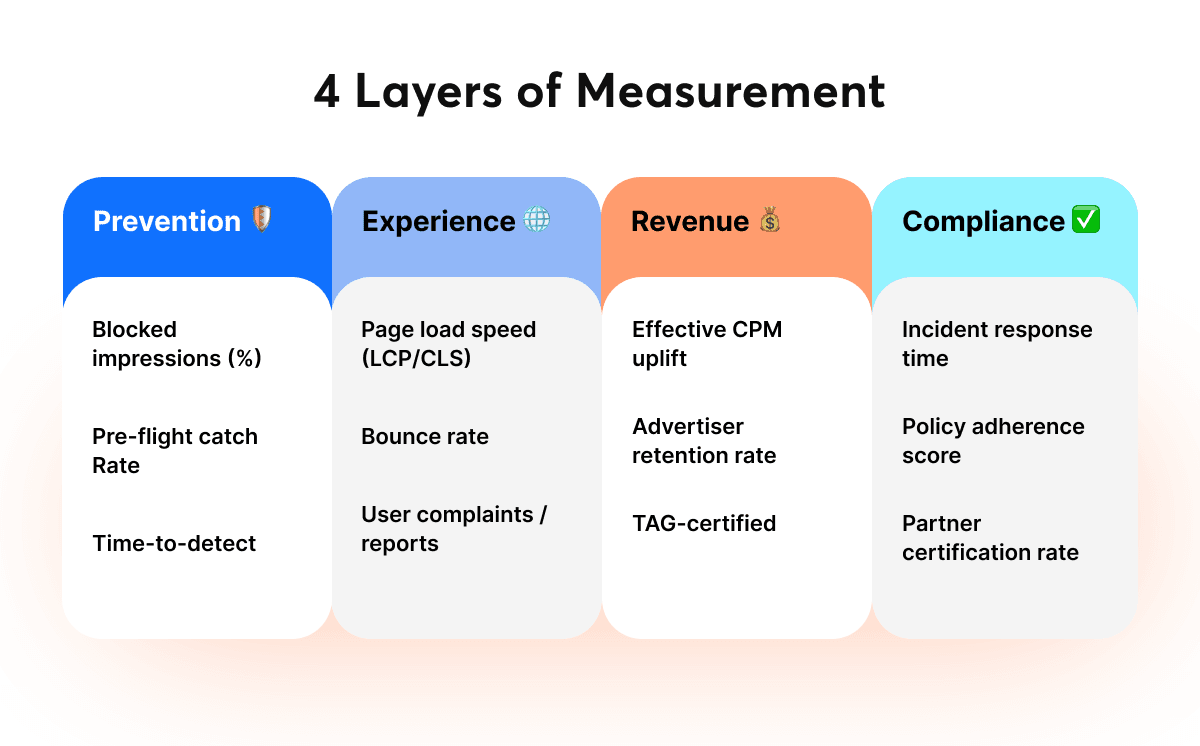
1. Prevention Metrics
The most obvious success signal is simple: how much fraud you’ve stopped before users ever saw it.
Key metrics to monitor:
- Blocked impressions (%): Share of total impressions automatically stopped before delivery.
- Pre-flight catch rate: Ratio of malicious creatives detected before campaign launch.
- Time-to-detect: Average time between fraud attempt and mitigation.
Metric to watch: Aim for at least 90% of malicious creatives blocked pre-flight (MGID achieved this benchmark after integrating GeoEdge’s real-time scanning.)
2. Quality and Experience Metrics
Fighting fraud extends from defense to driving meaningful engagement. Cleaner ads load faster, users stay longer and publishers earn more.
Track these:
- Page load speed (LCP/CLS): Average page performance metrics, improved through limiting heavy or intrusive ad elements
- Bounce rate: Share of sessions ending after a single page view, expected to decrease as disruptive formats are filtered out
- User complaints or ad report volume: Count of user-reported ad issues, serving as a qualitative indicator of trust and experience quality
Metric to watch: Aim to keep LCP under 2.5 seconds. This maintains the threshold for a strong user experience and better engagement.
3. Revenue and Efficiency Metrics
Fraud prevention pays for itself when budgets stop leaking. Focus on metrics that link clean inventory to profitability.
Measure:
- Effective CPM uplift: Difference in average CPM between verified and non-verified inventory, reflecting the added value of clean supply
- Advertiser retention rate: Share of advertisers renewing or extending campaigns, driven by trust in a transparent ecosystem
- Share of TAG-certified traffic: Portion of total traffic meeting industry verification standards
Metric to watch: Aim for a 10–15% eCPM uplift on verified inventory, which signals clear business impact from maintaining a fully transparent and trusted supply chain.
4. Compliance and Trust Metrics
Finally, measure the intangible benefits: transparency, reliability, brand safety. Because in 2025, these aren’t soft KPIs anymore.
Key metrics to monitor:
- Incident response time: Average duration from fraud detection to full public resolution
- Policy adherence score: Internal metric tracking compliance with IAB/MRC standards
- Partner certification rate: Percentage of SSPs, DSPs and advertisers verified through KYC/KYB processes
Metric to watch: Aim to resolve verified incidents within 24–48 hours and maintain a 100% certification rate among core partners to uphold trust and compliance across the supply chain.
Chapter 8
Policy, Standards & Industry Initiatives
Ad security doesn’t exist in a vacuum. Every scan, certification and blocked impression sits within a broader context, one that unites technology, policy and shared accountability.
In 2025, the global advertising industry has made major strides toward building a common compliance language. Frameworks like TAG’s Certified Against Fraud (CAF), IAB’s Transparency Center and MRC’s accreditation standards are setting the rules of fair play. However, those rules only work when companies apply them in real time, at scale.
That’s where the MGID × GeoEdge model becomes a blueprint for the future: it’s compliance in action.
Instead of treating standards as checkboxes, MGID and GeoEdge embed them into the very architecture of the ad delivery process, from KYC/KYB verification to AI-driven creative audits and live malvertising detection.
How it all connects:
- TAG/CAF: Define who’s trustworthy.
- IAB/MRC: Define how to measure and prove trustworthiness.
- MGID×GeoEdge: Ensures trust at every millisecond.
This alignment reflects not only good governance but also sound business sense.
According to IAB Europe’s 2025 Transparency Report, advertisers are already shifting 40% more budget toward certified and verified supply paths, prioritizing partners who can prove compliance rather than just claim it.
So the next frontier is compliance by default. As AI becomes standard in ad operations, compliance will move from manual checks to automated integrity systems, scanning every creative, landing page and supply chain partner before an ad ever goes live. In that world, fraud prevention defines the foundation of the open web’s sustainability.
Chapter 9
Glossary & Appendices
Ad fraud
Any deliberate attempt to deceive ad platforms or advertisers for financial gain — including fake impressions, clicks, installs or conversions
Invalid Traffic (IVT)
Any ad interaction that doesn’t come from a real user
- GIVT (General Invalid Traffic): Simple, easy-to-detect fraud — such as known bots or data center traffic
- SIVT (Sophisticated Invalid Traffic): Complex, human-like traffic generated by advanced bots, emulators, or spoofed devices
Malvertising
Malicious or deceptive advertising that injects harmful code, redirects users or promotes scams through legitimate ad placements
Cloaking
A technique where an ad shows different content to reviewers and real users — often using scripts or AI to disguise fraudulent or policy-violating material
SSAI Spoofing (Server-Side Ad Insertion)
A CTV fraud method where fake ad requests are generated by mimicking legitimate video streams, creating the illusion of real viewers
Made-for-Advertising (MFA)
Low-quality websites built mainly to host ads rather than deliver content. While MFA isn’t always fraud, it wastes budgets and weakens user trust.
Redirect Attack
A type of malvertising that automatically sends users to another (often malicious) website without their consent
Heavy Ads
Creatives that exceed Chrome’s resource limits (CPU, network or memory), slowing down pages and harming UX
Floating Ads
Overlays that cover page content and follow users as they scroll — technically legal but often cited as intrusive or deceptive
KYC / KYB
“Know Your Customer / Know Your Business” — verification processes ensuring advertisers and partners are legitimate and compliant
TAG / IAB / MRC / CAF
Industry organizations and standards that define and certify responsible advertising practices:
- TAG: Trustworthy Accountability Group — anti-fraud certification and transparency
- IAB: Interactive Advertising Bureau — policy and framework leadership
- MRC: Media Rating Council — accreditation for ad measurement standards
- CAF: Certified Against Fraud — TAG’s global program for supply chain integrity
Chapter 10
The Clean Signal: Where Trust Meets Technology
Billions of ads fight for our attention every day, blurring the line between connection and deception. But 2025 also marks a turning point: the moment the industry finally began treating ad quality not as an afterthought but as the foundation of growth.
Every verified impression, every blocked redirect, every clean landing page sends a single message through the noise: trust still matters. Through the partnership between MGID and GeoEdge, technology and integrity have become inseparable.
AI now powers and protects every campaign. Compliance runs through every step of the process. Ad security has become the new currency of the open web. The clean signal travels further than any click. It builds audiences that stay, brands that grow and ecosystems that last.
As the digital landscape keeps evolving, one principle remains constant: real results can only come from real experiences and real users.
That’s the promise of secure advertising, and honoring this promise is how we keep the web open, transparent and human.